This is a 5 part series on why GPU clusters are under-utilized, how to measure utilization and how to improve it.
Part 1 - Why is your GPU cluster idle
Part 2 - How to measure your GPU utilization
Part 3 - How to fix your GPU utilization
Part 4 - GPU security and Isolation
Part 5 - Tips for optimizing GPU utilization in Kubernetes
GPU security and Isolation
Effective GPU resource management provides significant security and isolation benefits beyond simple cost optimization. These benefits become increasingly important as organizations deploy GPU workloads across multiple teams and projects.
Hardware-Level Isolation with MIG
Multi-Instance GPU (MIG) technology provides hardware-level isolation, enabling secure multi-tenancy on expensive GPU hardware. MIG partitions create isolated GPU instances with dedicated memory and compute resources, thereby preventing workloads from interfering with each other.
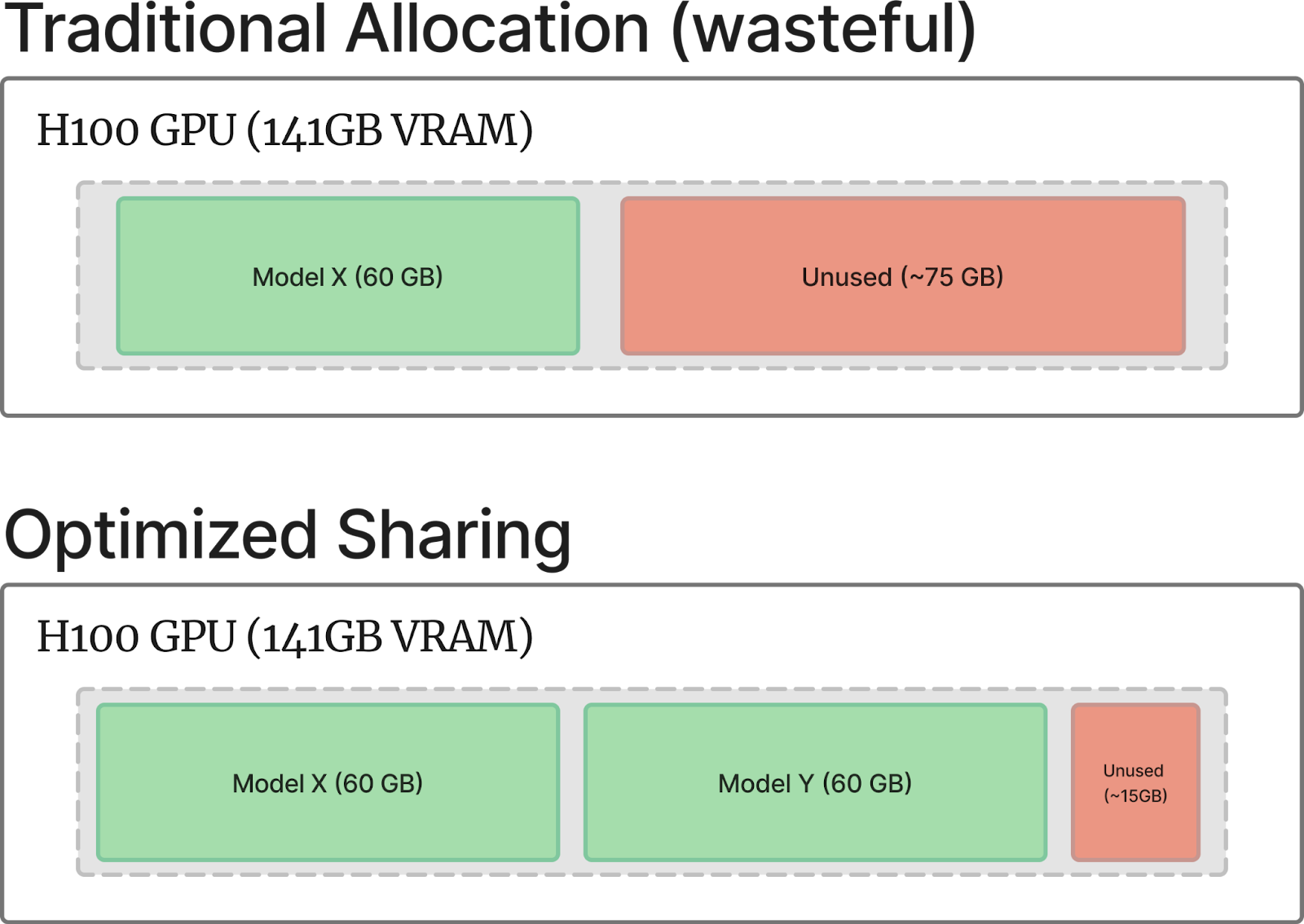
MIG partitioning strategies depend on workload requirements:
- Development and testing: Smaller MIG instances for multiple concurrent experiments
- Production inference: Larger MIG instances for performance-critical workloads
- Multi-tenant environments: Balanced partitioning for different teams or projects
Multi-Tenancy Patterns
Different organizational contexts require different multi-tenancy approaches:
Department-level isolation: When multiple departments share GPU infrastructure, hardware-level isolation through MIG or dedicated nodes may be necessary to prevent resource conflicts and ensure security boundaries.
Team-level sharing: Within engineering organizations, memory-based sharing may be acceptable when teams work on related projects with compatible security requirements.
Project-level optimization: Short-term projects may benefit from time-multiplexed sharing that maximizes utilization while maintaining project isolation.
Security Considerations
GPU workloads often process sensitive data or proprietary models that require additional security measures:
- Model protection: Preventing unauthorized access to trained models
- Data isolation: Ensuring training data doesn't leak between workloads
- Access controls: Managing who can deploy and access GPU resources
- Audit trails: Tracking GPU usage for compliance and security monitoring
Join our upcoming workshop with NVIDIA to learn more about GPU utilization for Kubernetes. Register here.